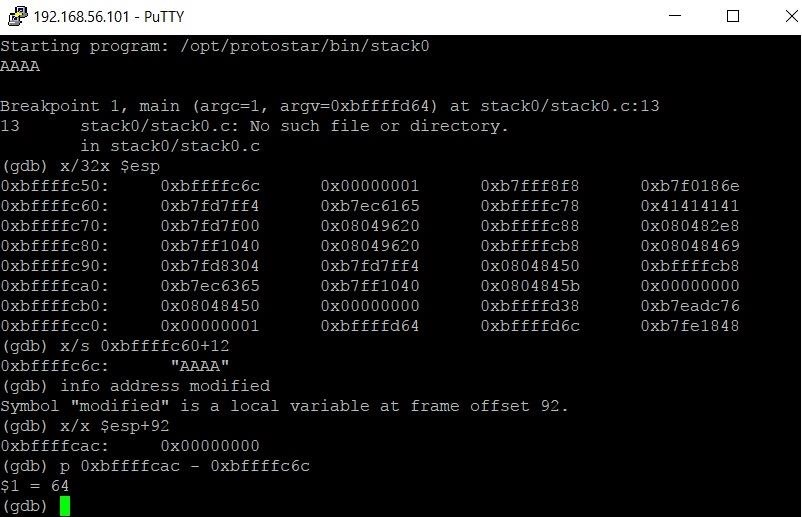
basic file exploit(100 points)— Binary Exploitation writeup | Pico CTF 2022 | by Karthikeyan Nagaraj | InfoSec Write-ups
Useless Crap? No, not nearly! Advance your binary exploitation skills by solving a sophisticated CTF challenge – HackMag