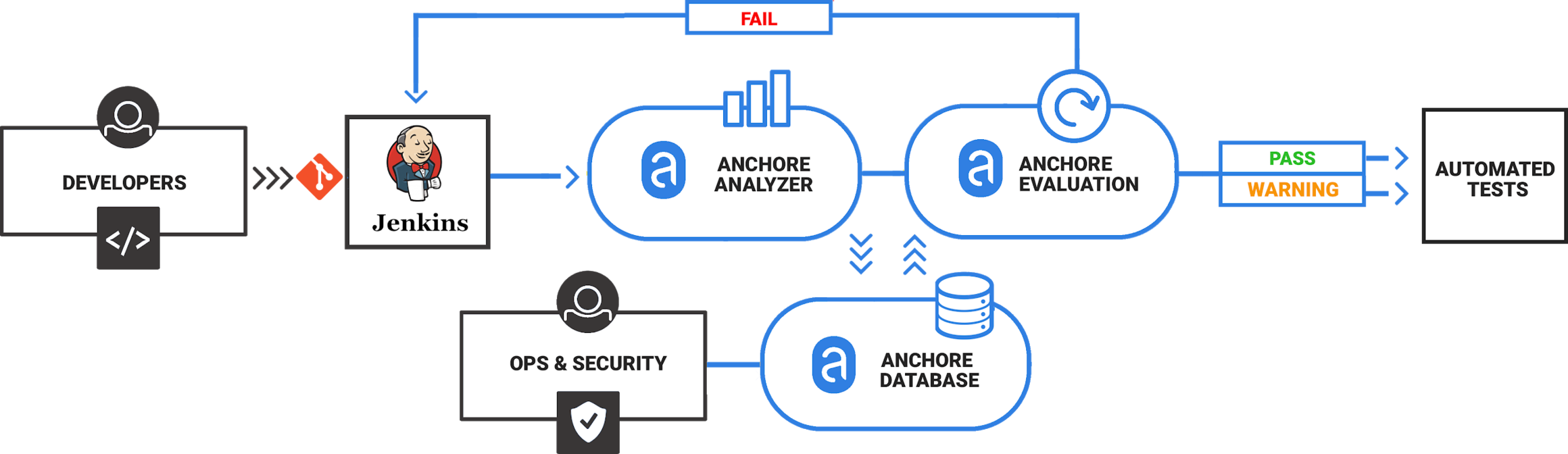
Scanning Docker Images for Vulnerabilities: Using Trivy for Effective Security Analysis | by Ramkrushna Maheshwar | Medium

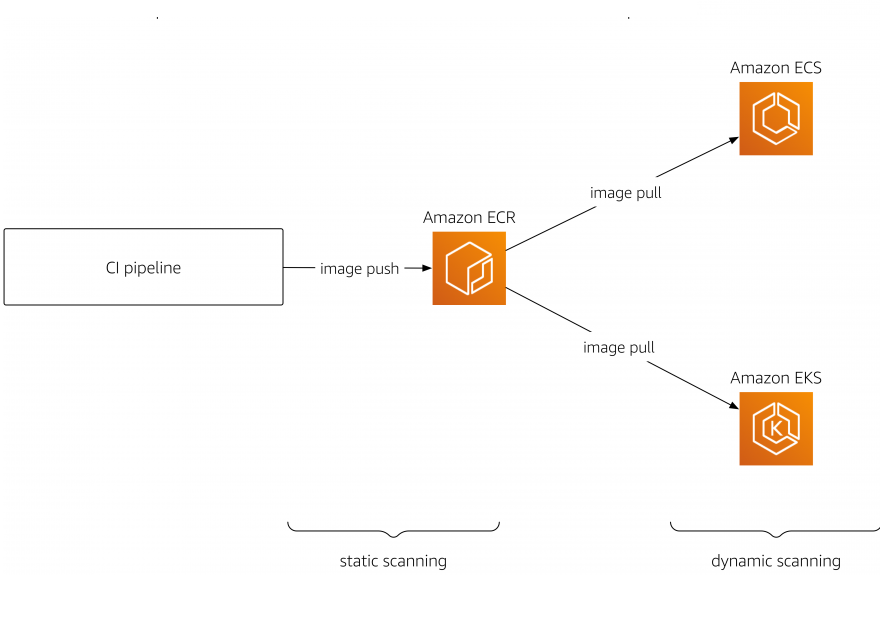
Guard against security vulnerabilities in your software supply chain with Container Registry vulnerability scanning | Google Cloud Blog
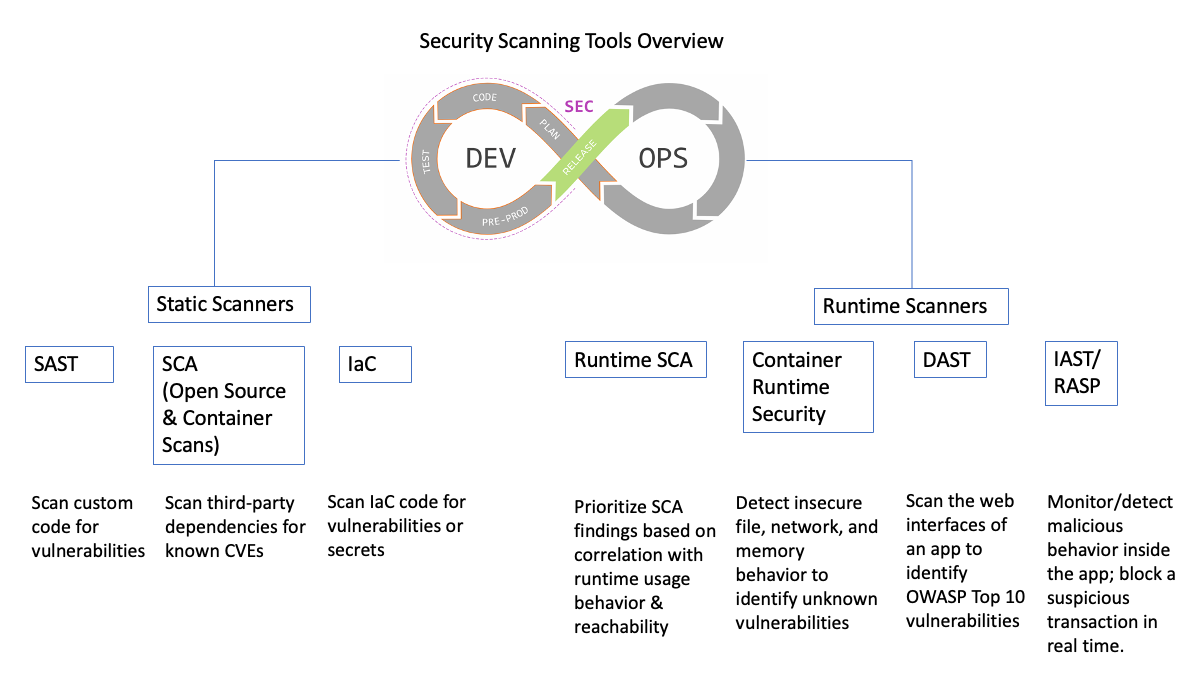
Security Scanning Tools Defined: SAST, IaC, SCA, DAST, IAST/RASP, Container Runtime Security and Runtime SCA - Deepfactor

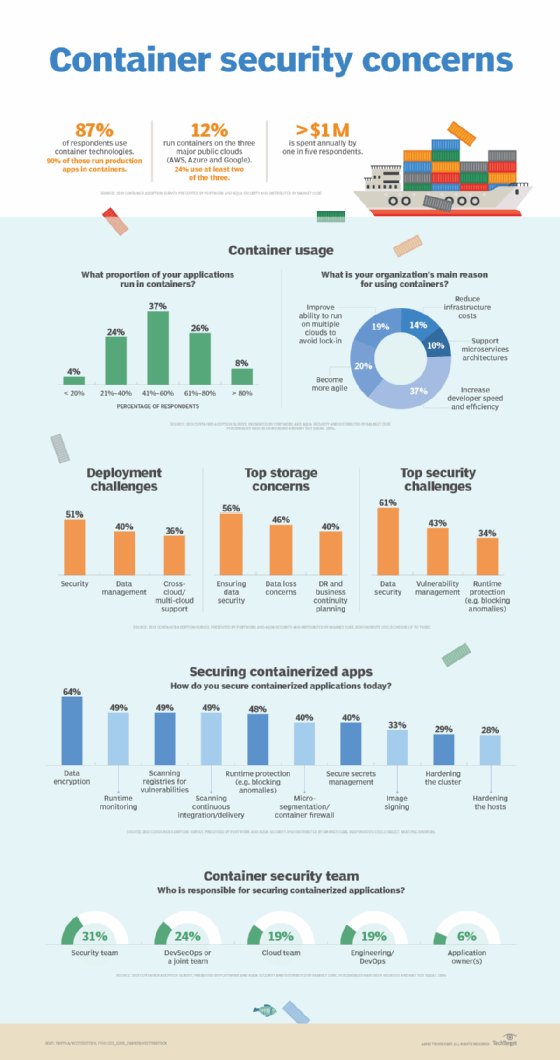
Docker Vulnerability Scanning Tools: Free, Open-Source, and Paid Options for Secure Container Images | by Hinanaseer | Medium
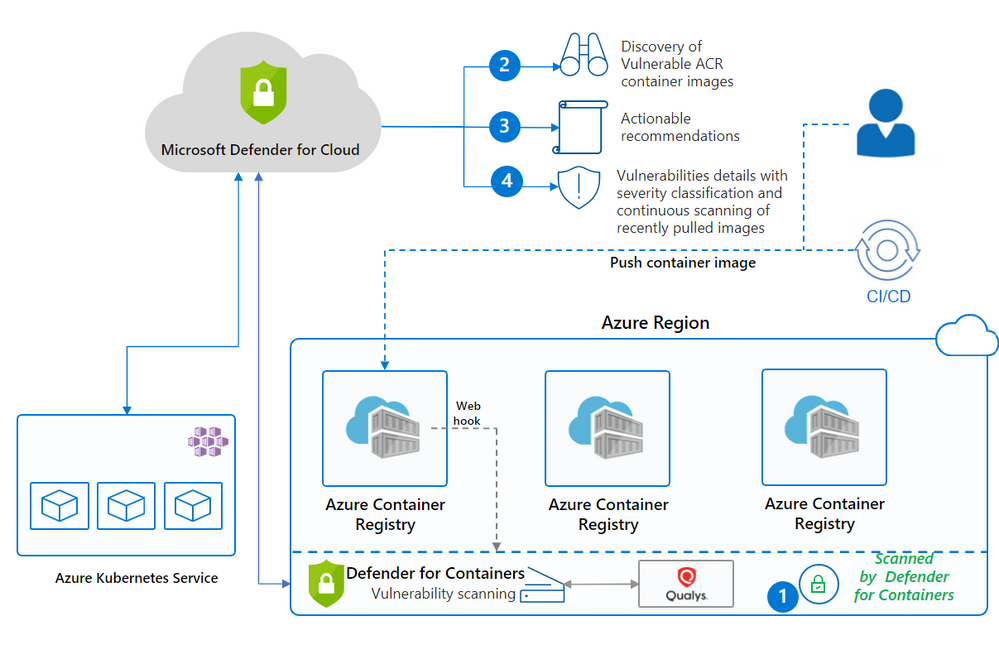
Enhance your CI/CD deployment by using Vulnerability Assessments from Microsoft Defender for ACR - Microsoft Community Hub